Duane was thrilled to be starting his new job. He was already five years into his development career and while he had worked in a number of different areas, he hadn't spend any "professional" time in the one area he was most passionate about: security.
This is not to say that he hadn't spent a lot of his spare time learning as much as he could about various aspects of security. But it is difficult to find a job in the security field when the only mention of 'security' on your resume is in the "Hobbies" section.
That was why he took this position with BGD (Big Government Department). When Duane starting passing his resume around, he had instructed his recruiter to focus only on jobs where security played a major factor. Yes, this increased the time it took to find positions. And he spent many of his interviews trying to convince potential employers that he really did have the security chops. So when the interview with BGD had focused extensively on defensive coding techniques, the performance of different encryption algorithms, and two-factor authentication patterns, Duane was very interested. And when he received the job offer, he was nearly beside himself with excitement.
And so here he was, on his first day, looking at the following Microsoft Access VBA macro that his boss had given him as an example of the style of coding he would be expected to produce.
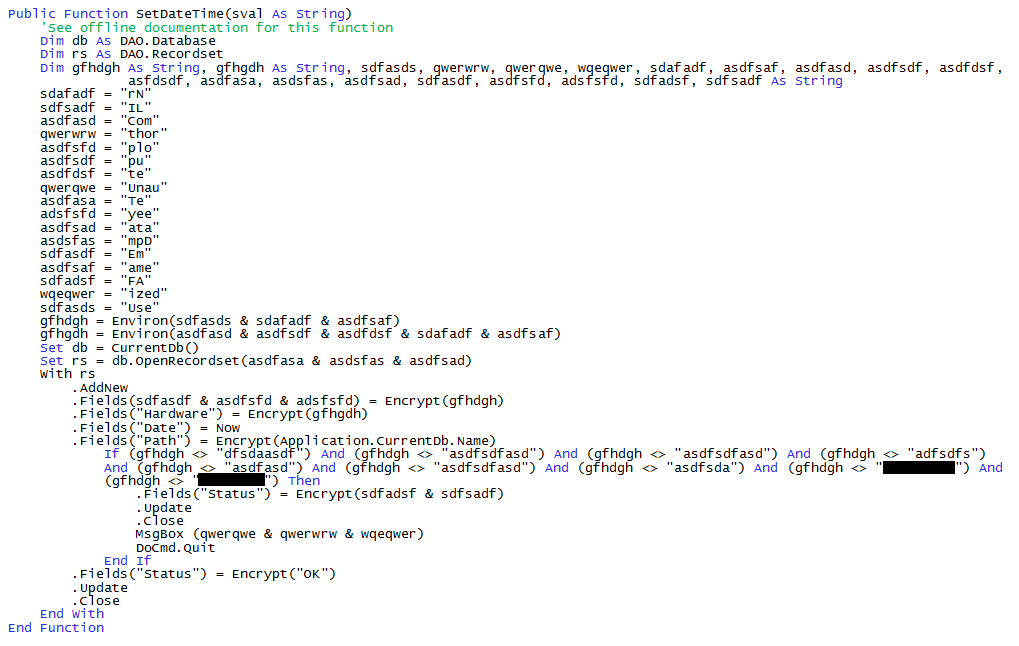
After a few moments of head-scratching, gut-churning perusal, Duane walked into his boss' office.
"About this code", Duane started
"Yes?", said his boss
"Um...Can you explain the reasoning behind it?", ventured Duane. "I mean, I can tell from the title that it sets the date and time. But why do it this way?"
"Well, it's really quite simple", started his boss. "As you know, security here is one of our most important concerns. And this database is used in each of our branch offices. Management was concerned that the names of the recordsets that are used would be visible to the users. And if they knew the recordset names, they might start to look at the data."
"But doesn't the macro just grab information from the Tem...pD...ata recordset?, asked Duane.
"Why, yes...yes it does", came the reply. Without the sarcasm that Duane was hoping for.
"O...kay. What about this line here", Duane said, pointing at the first line that uses the Environ function. "Why are you worried about them knowing that the macro uses the Use...rN...ame system value?"
"Don't be silly. We know we can't keep them from knowing. It's just that we don't want to make it easy for them", countered his boss.
"Um...fine. Then why is it that you included the names of the users that are authorized to change the date and time in plain text". paried Duane.
(Author's note: the names of the users were changed as part of the submission. The redactions were done by the submittor as well. I found it ironic that scrambling some of the user names was sufficient for *most* of the values in the submission...but not all)
"Easy", said his boss with finality. "Even if they find this code, no user would be able to figure out what this method is doing."
Duane walked slowly back to his office and slumped into his chair. After a few moments of anguished decision-making, he reached into his pocket, pulled out his cell phone and placed the call he now knew was inevitable. To his recruiter.

