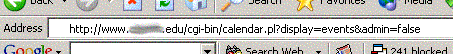My email seems to be down for now, so today's “good practice“ example comes from yours truly. A software tester I work with was pretty excited that he was able to hack a web-based calendar application built for a college. The system was in production for a while, and he was supposed to test a minor tweak made to it. Now, I'm not going to tell you how he gained administrator privileges, but I will present the URL of the system and see if you can figure it out:
The system was quickly secured by making “admin“ a hidden form variable. While I doubt you fellows would be able to hack that, I blurred out the university name just in case. We wouldn't want “Panty Raid at Heinsmans!!!” listed under “Alumni Council Meeting” now would we?
-- Don't forget to send in your Daily WTF!