 "I have been helping a guy with a project," seebs wrote, "I wasn't originally involved, but when the three-month project was six-months late, I got called in to start on the other half. I still remember the sick feeling in the pit of my stomach when the developer told me "all fields are varchar for simplicity...'"
"I have been helping a guy with a project," seebs wrote, "I wasn't originally involved, but when the three-month project was six-months late, I got called in to start on the other half. I still remember the sick feeling in the pit of my stomach when the developer told me "all fields are varchar for simplicity...'"
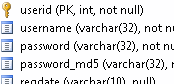
"There's a database of users who can log in. Now, we all know that you always store the password encrypted, right? Perfect, it's stored as MD5. Here's the three relevant fields in the database:
username VARCHAR(32), password VARCHAR(32), password_md5 VARCHAR(32)
"...And yes," seebs continued, "the 'password' field holds the password in plaintext."
"Amazingly, the MD5 password is even calculated using a salt key. It's the MD5 hash of salt + name + password. The salt is the name of the company the project is for. Well, no. It's a misspelling of the name, with two typos out of six letters. Now, I'd have thought this might be intentional, except that two of the states a transaction can be in are CANCELED and CANCELLED_TX.
"The whole thing is like this. Several megabytes of code.

