To help ring in the new year, here - enjoy this "Best of WTF" classic that ran in 2014!
Tom works as a pentester and, as such, gets paid big bucks for finding flaws in his clients' websites usually because he has to find less than obvious 'gotcha'-level flaws.
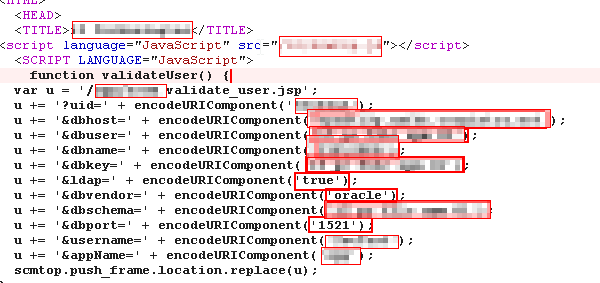
While testing a critical web application for a very large corporate client, he noticed some odd behavior surrounding a page that validates user logins.
Apparently, the original developer decided that it would be a good idea to send the database credentials to the client in a snippet of JavaScript and then use them to formulate a GET request to the server, presumably where the user is validated.
I'm not sure what other surprises Tom found while working for this particular client, but I hope the developer's reach was mercifully limited.