How Many Times Do I Have to Tell You?
by in Error'd on 2007-11-30Reverse psychology is hard to resist, especially when it comes at you fourfold.
(submitted by Zach)
Reverse psychology is hard to resist, especially when it comes at you fourfold.
(submitted by Zach)
Brian works for a web development shop with an all-too-common formula: lots of intern labor and a very high turnover. As a recent hire, a large part of Brian's job is maintaining old sites developed by various former employees.
"I was recently asked to investigate a bug," Brian wrote, "where selecting a few publications from a multi-list caused strange errors and didn't store them correctly. When I initially went to check on the error, I noticed absurdly high "values" assigned to the problematic publications..."
For several days, Rick was fighting with a third party vendor. Rick's system was supposed to talk to his vendor's system using XML files, but their files were coming back with invalid XML data. Rick complained to a technical contact ("Terry") that the XML they returned was invalid. Terry argued that they were processing the file wrong.
The issue that Rick discovered was that one of the attribute values in the XML file used single quotes instead of double quotes. Terry insisted that the XML file used only double quotes, and made his case by sending over screenshots from XMLSpy and IE, showing that they were indeed double quotes. The screenshot from IE would've looked something like this:
Finally, thought Marcin, a company that takes "landscape" literally.
When Andy G opened up libsymblogy.h (sic), he was relieved. Finally, some documentation! Of course, upon further inspection, Andy realized that the comments didn’t quite explain how the code works, how it interfaces with other modules, or even why it uses certain magic numbers like -13. Instead, every function had a comment just as hyperverbose and vapid as this…
// Description: Implementation of a C function having the special purpose of // initializing three particular ex ternal structure elements with arrays of // stored values which define all symbol modifiers for a corresponding symbology // datatype, i.e., airborne, land and naval platforms, sensors/emitters, etc. // The function's input parameters represent the location of the stored data and // the type of symbology the instructor/operator desires to view. The function // operates on the presumption that these parameters are valid. The function // first opens the stored data file and clears the appropriate symbol modifier // structure depending on the given datatype. Then the function populates three // lookup tables with 1) stored indices destined for use as symbol modifiers, // 2) stored ASCII representations of each symbol modifier row, and 3) stored // ASCII representations of each symbol modifier column. The function's output // parameters represent the filename, section, record and datum which was last // read from the symbology datafile, if any. The function returns a byte // value 0 when the desired symbol modifiers are successfully initialized. // Otherwise, the function returns a byte value -13 if the symbology datafile // doesn't contain the symbol modifier data
 Not too long ago, The Powers That Be in the emerging eastern-European country of Latveria (as I’ll call it) decided that the time had come for a massive, central monitoring system that would be used to ensure the country’s security. SENTINEL, as the system would be called, involved data exchange between virtually every governmental agency, airports, financial institutions, transit systems, and so forth, all for the purpose of being able to track people and the money they spend. After well over a year of negotiations, The Powers That Be selected Christian B’s company to design SENTINEL’s enterprise architecture.
Not too long ago, The Powers That Be in the emerging eastern-European country of Latveria (as I’ll call it) decided that the time had come for a massive, central monitoring system that would be used to ensure the country’s security. SENTINEL, as the system would be called, involved data exchange between virtually every governmental agency, airports, financial institutions, transit systems, and so forth, all for the purpose of being able to track people and the money they spend. After well over a year of negotiations, The Powers That Be selected Christian B’s company to design SENTINEL’s enterprise architecture.
Over the next year or so, Christian got accustomed to the weekly Latverian commute: wake up at 4:00 AM on Monday, depart from Paris via airplane, arrive in Hassenstadt (Latveria’s capitol) several hours later, work five twelve-to-fifteen hour days, catch a plane back home, and sleep until noon on Saturday. He also got very accustomed with Latverian politics: The Powers That Be, especially those from the Ministry of Defense, were personally involved with almost every decision at every level. And they didn’t take criticism very well. One network engineer was fired on the spot (and some suspect, later executed) for disagreeing with a Latverian director.
Joshua had recently started his job at a consulting firm. To get his feet wet, he was added to the team on an application they maintained for the juvenile court system. Fortunately, it had been developed entirely by the company, and everyone Joshua had met at the company seemed to have a good head on their shoulders. Plus it wasn't too big of an application, making it an ideal environment for Joshua to learn.
Joshua's first task was to prepare some reports for the users — an ideal first task for a developer new to a system. Except that it was practically impossible to create the reports they wanted.
"I'm sorry, we don't have X, would you like X instead?"
(submitted by Mike D.)
Finding bad code in some old system you’ve come to maintain is one thing. Being tasked with adding bad code to a new system is a whole other type of pain. Paul G was lucky enough to experience this first hand.
After an hour or two of arguing that there is a better way of doing this, Paul wrote, I was overruled by the longest serving developer and, as a result, forced to write the ‘Remove Special Chars Except Quote Ampersand Apostrophe Open Bracket Close Bracket Comma Hyphen Full Stop Comma Forward Slash’ function. Seriously.
Edward F wishes that some products weren't quite that honest to him...
The Beat on the Street in Peterborough (England) is that Data Interchange is looking to hire Software Developers. And I mean “on the street” quite literally:
“Ummm…” the top email in Alex M.’s inbox started, “why did you delete my message about the approval bug? And then delete the message inquiring about the deletion? This issue isn’t going away – please investigate this right away!”
Had this been the first like message Alex had seen, he might have been surprised. But it wasn’t. For the past several weeks, customers, vendors, coworkers, and anyone else who emailed him received some rather interesting status notifications regarding their message. It was seemingly random and consisted of replies like “your message was deleted without being read,” “your meeting request has been declined,” or even “I will be out of office for the rest of the day.”
Two faces or a vase? Half full or half empty? Singing or childishly mocking?
(submitted by Drew)
The idea behind “information hiding” – i.e. encapsulating certain methods and properties to users of a class – is a fair idea in theory, but in practice, it’s just too slow. Think about it. If a “public” method just ends up calling some “private” method, that’s just a waste of a call. And if a lot of calls are made to that public method, then that’s a whole lot of wasted calls!
Vlad’s predecessor knew this fact well when he was designing “safety critical” functions for his company’s ------ application. Instead of wasting precious CPU time on “information hiding”, he put in a simple request to users of his class…
"H... hello?" Cid groaned, looking at his clock. It was 4:53 AM.
"Hi, good morning, is this Cid? I hope I'm not waking you up."
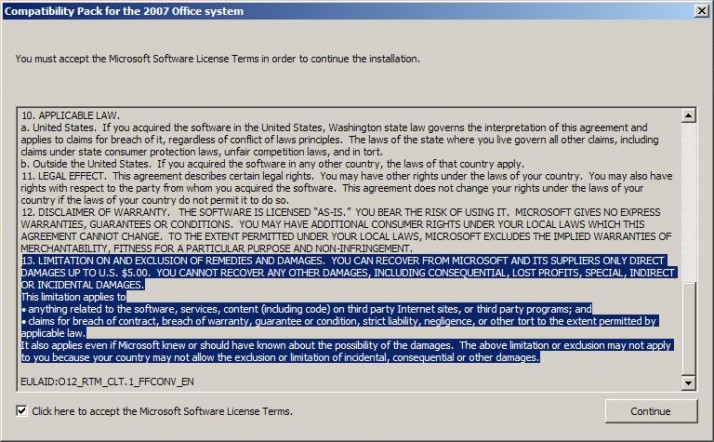
Eric actually read the EULA for Office 2007 Compatibility Pack, and was happy to know that Microsoft will actually take responsibility up to five whole dollars for damages to your computer...
After Travis took his new position he was amazed to find that the developers that he was replacing were completely unaware of the Date/Time library in the .NET Framework. Instead the relied upon time spans and complicated regular expressions for simple tasks, such as validating a string as a date...
 The transition from computer technician to software developer can be pretty rough. Not only does one have to give up the chic company car (and, of course, all the hot dates it guarantees), but he has to land that rare technician job that has just enough programming work to stretch his job title on a résumé to “programmer.” Garret was lucky enough to find that job at a small computer repair shop we’ll called “AAAA Computers”
The transition from computer technician to software developer can be pretty rough. Not only does one have to give up the chic company car (and, of course, all the hot dates it guarantees), but he has to land that rare technician job that has just enough programming work to stretch his job title on a résumé to “programmer.” Garret was lucky enough to find that job at a small computer repair shop we’ll called “AAAA Computers”
Garret’s official title AAAA Computers was “Technical Office Manager,” which came with a job description of “ya know, just do whatever it takes to run the shop ‘n stuff.” Being that Garret was the only employee at that location, this involved everything from fielding phone calls to sweeping the floors at night.
E. D. enjoyed a foreign film that was produced in a country that apparently communicates via special characters and fractions.
If you're good at what you do, you can judge when to employ which design patterns. And, on the other hand, when employing said design patterns would make the means too complicated to justify the ends. Dale M. sent in an example of this sort of overcomplication:
Interface: 10 lines (4 Lines Of Code w/o comments)
core/src/com/.../enterprise/util/codetable/IYesNo.java
Factory: 141 lines (69 LOC)
core/src/com/.../enterprise/util/codetable/YesNoFactory.java
(Note that the factory includes an inner class called YesNoInstanceType)
Abstract class: 43 lines (17 LOC)
core-restricted/src/com/.../enterprise/util/codetable/restricted/YesNo.java
Concrete class: 87 lines (61 LOC)
core-restricted/src/com/.../enterprise/util/codetable/restricted/nonpersistent/YesNo.java
 Developers-turned-dev managers often struggle to contain themselves when it comes to bug hunting. After all, they can usually resolve problems faster and better than the coders in their employ. The problem is, no developer wants a boss who takes more time explaining what must be done than it actually takes to do it. That leaves dev managers in the difficult spot of delegating the bug hunt and waiting for results.
Developers-turned-dev managers often struggle to contain themselves when it comes to bug hunting. After all, they can usually resolve problems faster and better than the coders in their employ. The problem is, no developer wants a boss who takes more time explaining what must be done than it actually takes to do it. That leaves dev managers in the difficult spot of delegating the bug hunt and waiting for results.
As a newly hired development manager of a travel-bookings system, Dan E. found himself in this very situation. Overseeing a crew that was maintaining a fairly large ASP/VBScript codebase, Dan wanted to stay close to the technical details of the project while giving his coders room to do their jobs. So he simply offered some suggestions on what might be causing various error messages to appear.
At first I was thrilled about the unexpected rate decrease, but leave it to AT&T to crush my excitement ...
This CAPTCHA stuff is getting ridiculous. What is this, like... underscore-hyphen-hyphen-accent-subscripted hyphen-underscore?
(submitted by Adrian K.)
 When Sergey L. showed up for his first day at his new job, he wasn't really sure what he'd be working on. The hiring manager wasn't very specific. "Database skills are very important," he told Sergey. "You'll be our first real sysadmin maintaining some stuff that a bunch of consultants set up."
When Sergey L. showed up for his first day at his new job, he wasn't really sure what he'd be working on. The hiring manager wasn't very specific. "Database skills are very important," he told Sergey. "You'll be our first real sysadmin maintaining some stuff that a bunch of consultants set up."
Sergey was the first sysadmin that the company had ever hired in its five year history. And no one was really sure what to do with him or where he fit in the environment. As such, he didn't really have a boss. He had a team of bosses. Specifically, everyone in the company.
Martin W. usually leaves for work at 8:00 AM, but he left a little later on April 18 due to "Martian storms and temperatures below absolute zero."
You've probably encountered more than your fair share of inadequately descriptive variable and function names. Debugging a function with variables named a, a1, a2, a0, aO, al, a1l, al1, aIl, a1I, and al1I is something I wouldn't wish on my worst enemy.
On the opposite end, we have this code from an anonymous submitter:
In the early 1980s, George C. was IT support on a team overseeing a large installation of workstations. At the time, this was a pretty novel concept. Several Unix site managers applied to help out but wanted "too much money," according to management. Instead, the IT manager rounded up a bunch of recent college graduates (who were much cheaper). Problem solved.
There were roughly 80 workstations that were being installed, each with two 70MB drives. One drive kept the operating system files (which the users couldn't modify), the other was the user drive for work files. Each system was backed up and updated nightly with a three step process:
Keep your fingers crossed that that F. B. won't have to pay the 2.25 million billion dollars. Or at least that he can pay in two 1.12 million billion dollar installments.
Suppose you're using C# and you have a bunch of RSS data that you want to sort and put into a file. Think about how you'd approach the task.
You might consider a generic list. Maybe a DataTable and a DataView. Guilherme's colleague decided on (and invented) the Multi Array Bubble Sort technique.
I think this is a case of the department responsible for spam filtering having a grudge against the copywriting department.
(submitted by Matt G.)
Most of the WTFs we get are like light snacks. Some programmer didn't know better, screwed something up, we laugh at it, and hopefully everyone learns something. Other times WTFs are Homerian epics. Today's story is one of those.
Jared L. is our Odysseus in this story. As a fresh college graduate, he landed a good position as a Java webmaster in charge of about 25 web sites. He'd never written a single line of JSP code in his life, but he figured he could pick it up pretty quickly. And during his interview he mentioned that he didn't have any JSP experience, but they made him an offer anyway — it wasn't like he'd lied about his experience level.