- Feature Articles
- CodeSOD
- Error'd
-
Forums
-
Other Articles
- Random Article
- Other Series
- Alex's Soapbox
- Announcements
- Best of…
- Best of Email
- Best of the Sidebar
- Bring Your Own Code
- Coded Smorgasbord
- Mandatory Fun Day
- Off Topic
- Representative Line
- News Roundup
- Editor's Soapbox
- Software on the Rocks
- Souvenir Potpourri
- Sponsor Post
- Tales from the Interview
- The Daily WTF: Live
- Virtudyne
Recent Articles
Security by Post-It
by in Feature Articles on 2011-04-28Over the years, we've seen some fairly interesting security principles discussed here on The Daily WTF. While most in the industry already appreciate the benefits of Security by Obscurity, readers like you have contributed some fascinating alternatives including Security by Oblivity, Security by Insanity, Security by Letterhead, and and Security by Posterity. Today, I'm excited to add a new strategy for securing information systems: Security by Post-It.
With the rash of high-profile breaches happening everywhere from credit card processors to government bureaus to gaming networks, many organizations are clamping down on security to make sure that everything feels extra-secure. Now granted, many of these break-ins are a result of SQL Injection, social engineering, and simply forgetting to check authorization rules, anything could be a vector of attack – including your very own mind.
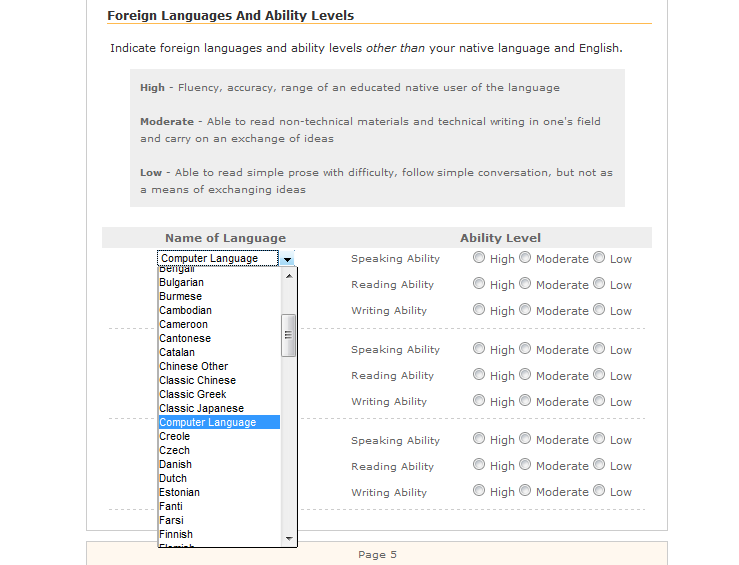
Email Validation Validity
by in CodeSOD on 2011-04-27There are a lot of different ways to validate an email address input field. The easiest – and mostly correct – method is to use a regular expression. Two of the more complicated – and among the most incorrect – methods follow.
Jonasfound this in a custom-built web app at a customer site, and commented that it's emblematic of the quality of the whole codebase.
SODEC 2011 (Japan)
by in Announcements on 2011-04-27I suspect this announcement will be even less relevant than the Detroit-centric announcement for Penguicon 2011... but here goes. For three of you that are reading The Daily WTF in Japan, I'll be headed out your way to attend SODEC from May 11-13.
Although this will be my first trip to Japan, I can assure you that won't be that gaijin guy. I am, after all, an expert in international language (i.e., raising my voice and SPEEEAAAKING VEEERRRYY SLLOOWWLY). Either way, I'll be chronicling my journey on Twitter (@apapadimoulis), along with a near-endless amount of pointless banter.
Reduhdant Power
by in Feature Articles on 2011-04-26 The ancient gods released their fury; wind and wrack raged outside. Wind and lightning smote the power to Hubert's office, plunging the offices and server room into darkness. Hubert was new to the company, and had never received any training on emergency procedures, but he did possess a degree of common sense. Instead of stumbling upstairs to the server room in the dark, he reached for one of the emergency flashlights and turned it on. Or tried to- the battery was dead.
The ancient gods released their fury; wind and wrack raged outside. Wind and lightning smote the power to Hubert's office, plunging the offices and server room into darkness. Hubert was new to the company, and had never received any training on emergency procedures, but he did possess a degree of common sense. Instead of stumbling upstairs to the server room in the dark, he reached for one of the emergency flashlights and turned it on. Or tried to- the battery was dead.
Hubert stumbled to the server room in the dark, guided only by the blinking lights of WiFi routers scattered throughout the building, or the faint hints of light from the windows. When Hubert reached the electronically locked door protecting the server room, it was, well, locked. That battery was still working, although it was anyone's guess as to when it was last replaced. The voltaic cell managed to cough up enough power to grind the lock back with the speed of a stone door in the Temple of Doom.
Units of Software
by in CodeSOD on 2011-04-21Marcus writes (via the Submit to The Daily WTF plug-in), "there are many days when I think that my company simply hired our development team because they were fast typists."
"It's not as if we're paid by the line of code, but our management team is run by a couple MBAs that love to quantify everything. And as we all know, nothing quantifies programmer productivity better than the 'units of software' delivered. And speaking of a unit of software, here's a valuable one put together by one of my more 'productive' colleagues.
The Sixth Guy, The Company Pond, and More
by in Tales from the Interview on 2011-04-19The Company Pond (from Adam)
Our company had one of those decorative ponds located in front of the building where people can gaze out their cubicles and dream of being outside. It looked nice enough, but it was disgustingly dirty with runoff and probably about half full of goose droppings.
I was interviewing a nice-enough woman for a position with our company when my receptionist sheepishly burst into the room.
The Nondeterministic Hash
by in CodeSOD on 2011-04-18The application that Sam F helps support acts as a sort of "parallel data entry" platform. Users from different parts of the world aggregate and enter all sorts of data from different sources. Duplicate data entry was fairly commonplace, but it was rarely a problem that running a few complicated scripts couldn't clean up later. And therein laid the problem: "later" sometimes meant days or weeks.
In an attempt to deliver more accurate data sooner, Sam's colleague was tasked with hashing the data upon entry and using it as a sort of "instant" comparison. The fix seemed to help: users were warned about duplicate data, and management was satisfied with the reduction in duplicate data.
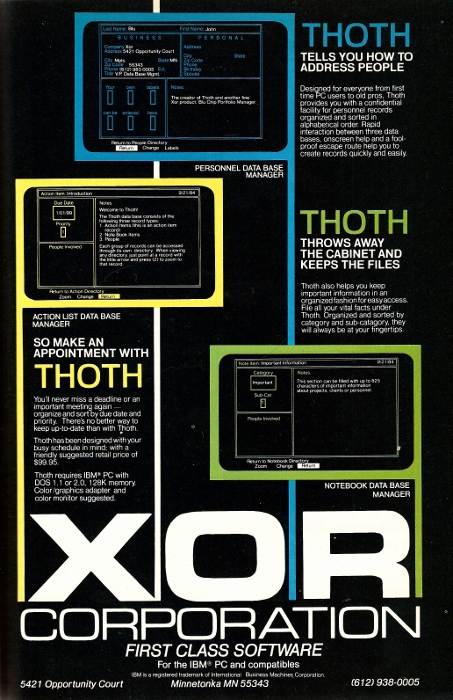
What the Ad?! - Maybe It Means 'Exclusive OR'
by in Feature Articles on 2011-04-14You may either use Thoth to manager your contacts and appointments...or another product...but never both.
Penguicon 2011
by in Announcements on 2011-04-13As I mentioned a few weeks back, I'll be headed to Notacon 8 a little later this week. If you're going, drop me a line and we'll grab a drink or something. And if you can't make it, not to worry - there's another event right around the corner. It's called Penguicon, and it's being held in Troy, Michigan from April 29 - May 1.
Penguicon is a unique blend of open source software and science fiction. When I first heard about it, I gave a Teal'c/Tuvok-esque eyebrow raise, and then realized, hmph... I guess there is a bit of an overlap. But it's a whole lot more than just that, as the events page shows. Take for example, this video from Penguicon 4 where Rob Landley (one of the co-founders) threw a bowl of liquid nitrogen into the hotel swimming pool.
A Char'd Enum
by in CodeSOD on 2011-04-13Ah yes, the enum. It's a convenient way to give an integer a discrete domain of values, without having to worry about constants. But you see, therein lies the problem. What happens if you don't want to use an integer? Perhaps you'd like to use a string? Or a datetime? Or a char?
If that were the case, some might say just make a class that acts similarly, or then you clearly don't want an enum. But others, such as Dan Holmes' colleague, go a different route. They make sure they can fit chars into enums.
Contract Termination
by in Feature Articles on 2011-04-12"It's a module to turn AS/400 flat files into XML. How hard could it be?"
A week into his one-year contract, Bobby suspected that statement would be his epitaph. As a contractor, you can only do so much recon before you walk into a job. You miss little things, like the fact that the IT manager you'll be working for and the IT manager that hired you are locked in a death-struggle, and you're little more than an artillery shell lobbed over the cubicle wall.
The Qualities of Equality
by in CodeSOD on 2011-04-11With complex datatypes, objects references, internalization, and all the other intricacies that go into modern day software development, the matter of equality is often a bit more involved than simply ==. Or at least it can be made to be, as today's two examples demonstrate.
First up is Willy's specimen, who adds "I particularly enjoy understatement of the comments in the dateAreEquals() and equals() methods.
Just-In-Time Business Cards
by in Announcements on 2011-04-07As you may have noticed, I am a big fan of souvenirs, trinkets, and tchotchkes. And I know I'm not alone. Whenever I go to a conference, at least half of my fellow attendees join me in the pursuit for as much free stuff as possible.
Of course, it doesn't matter that I already have enough logoed pens and pads to write the entire contents of Wikipedia, twice over. Or that I have enough tee-shirts to wear a new one every day for the rest of my life (and that's assuming I live to be a hundred and fifty). No, this epic quest for swag is about something different. Something grander... and perhaps, even primal.
The Phantom Password
by in Feature Articles on 2011-04-07“Before I broke into the IT racket,” Scott Simons writes, “I was a front-line Customer Service Rep. At the time, the procedure for logging into our service management system was a bit puzzling.”
“Like many organizations, your User ID was assigned by the company, but you had to choose your own password. But instead of having a screen to do that, you had to fill out a Password Request Form and fax it corporate headquarters. And then things got strange.
The Shortcut Guy
by in CodeSOD on 2011-04-06"My official title is Junior Developer," writes J Banic, "but I've come to become known as The Shortcut Guy. Why? Because I tend to know a lot of 'shortcuts' that the mid- and senior-level developers haven't yet discovered."
"To give you an idea at the type of 'shortcuts' I help them with, following is an instant message exchange between me ('jbanic') and a colleague ('mroot')."
mroot (10:03 AM): Got a problem for ya...
mroot (10:03 AM): Any idea how I can parse a string of email addresses like this:[email protected]@[email protected]?
mroot (10:04 AM): I need them separated in an array. I was thining of looking for .net, .com, etc.
jbanic (10:05 AM): That's not really feasible... you'd have to know *all* existing domains.
mroot: (10:05 AM): Is there a web service to do that?
jbanic (10:06 AM): Ehhh... no.
mroot: (11:18 AM): Okay. What if there was a comma between the addresses? For example,[email protected],[email protected],[email protected].
mroot: (11:19 AM): That should be easy to put in an array?
jbanic (11:22 AM): Waitasec... how did you add in the comma like that!?
mroot: (11:24 AM): I just copy/pasted them from debug console. That's what my string has.
jbanic (11:25 AM): Hmm... can you send me the code?
mroot: (11:25 AM): Sure, no problem...
mroot: (11:25 AM): Here it is.
Accessing the Portal
by in Feature Articles on 2011-04-05A new job is like a child. At first, it appears completely harmless and full of wonder. It's only after you've invested grinding years of your life into it, surrendering sleep and any sense of fun, that you discover that it's a complete disappointment and will never amount to anything, never respect you, and it certainly isn't going to take care of you during your twilight years.
Chuck's first day at his new job was much like that. He whistled a cheerful little tune as he walked across the parking lot. There were no first-day nerves. He looked forward to the day. The company ran clinical drug trials, so he felt like he might be doing some good in the world. The co-workers he had met while interviewing seemed like good people. Plus, he'd get to brush up his .NET chops. It wasn't a dream job, but it looked like a pretty good place to work.
Important-Function(), IsNumber(), and More()
by in Coded Smorgasbord on 2011-04-04" "I found a function called 'Important-Function' in a colleague's PowerShell script," wrote B. Versteylen, "after expanding the function, I discovered this."
Function Important-Function()
{
#Hehehehehehe ^^
$logTime = Get-Date -Format "yyyy-MM-dd HH:mm:ss" #Just so it looks the same as a regular log entry :+
$randomNumber1Method = New-Object System.Random
$randomNumber1 = $randomNumber1Method.Next(1,100)
If ($randomNumber1 -EQ 30)
{
$randomNumber2Method = New-Object System.Random
$randomNumber2 = $randomNumber2Method.Next(1,15)
Switch ($randomNumber2)
{
1 {Write-Host $logTime "Watching a colleague pick his nose..."}
2 {Write-Host $logTime "Solving a binary sudoku puzzle..."}
3 {Write-Host $logTime "Hoping to return anything useful..."}
4 {Write-Host $logTime "Slapping random people with a trout..."}
5 {Write-Host $logTime "Surfing porn sites on the internet..."}
6 {Write-Host $logTime "Pondering the next move..."}
7 {Write-Host $logTime "Formatting the hard drive..."}
8 {Write-Host $logTime "Dividing by `$null..."}
9 {Write-Host $logTime "Getting a cup of coffee..."}
10 {Write-Host $logTime "Trying to fit a square into a circle..."}
11 {Write-Host $logTime "Yawning as a cow races by..."}
12 {Write-Host $logTime "Milking a goat..."}
13 {Write-Host $logTime "Playing rock-scissors-paper..."}
14 {Write-Host $logTime "Reading a manual on WMI..."}
15 {Write-Host $logTime "Thinking about Jessica in Berlin..."}
}
}
}
Attributed to Malice
by in Feature Articles on 2011-04-01 Sometime around midnight...
Lorne: And so another April 2nd begins. Hope you enjoyed all three articles this April 1st. What, three of them? Yup. I guess you're one of the, like, 3 people who didn't figure out by hacking the site / clicking View Source.
All three articles are now display:block for your viewing pleasure. Thanks to Alex for throwing his sabos into the "RSS Factory", and for letting me indulge in a bit of mischief. Half the fun was trying to subvert the article system. The other half was researching wood-analogs for human bone. (I'm a writer. I really like research. It's like constructive procrastination).
For the record, two of the three articles are fakes. The screen shot is not from a real blade sharpening system, and no one had their dev servers bombed as "a test".
That bit of php, though? Paraphrased nearly line-for-line from a system I worked on once. Oh, memories. Painful, painful memories.
- Lorne, April 1, 2011
(PS: Svengali is real, and his show is better than Cats. You should go see it, again and again.)
Today's storystories comes to us from Svengali:

 Mar 11
Mar 11