- Feature Articles
- CodeSOD
- Error'd
-
Forums
-
Other Articles
- Random Article
- Other Series
- Alex's Soapbox
- Announcements
- Best of…
- Best of Email
- Best of the Sidebar
- Bring Your Own Code
- Coded Smorgasbord
- Mandatory Fun Day
- Off Topic
- Representative Line
- News Roundup
- Editor's Soapbox
- Software on the Rocks
- Souvenir Potpourri
- Sponsor Post
- Tales from the Interview
- The Daily WTF: Live
- Virtudyne
Recent Articles
The Plural of Virus is not Virii
by in Feature Articles on 2011-07-28The life of a contract killer is hard. The life of a contract network admin is possibly harder. Guillermo juggled a set of contracts with local businesses that needed help but couldn't afford a full time network administrator. This meant he was not merely a network admin, he was six network admins, often with overlapping hours.
One afternoon, he did a routine series of checks on his largest client's Exchange server. Everything looked to be in order, but this company had a huge quantity of mail going in both directions. The virus scanner on the server had archived nearly ten thousand suspicious files, named "creative" things like hotxxx.jpg.exe. The disk was getting a little fuller than Guillermo liked, so he navigated to the quarantine folder and tapped "CTRL+A".
Representative Property: MaxRetry
by in CodeSOD on 2011-07-27"I’m a big fan of the Representative Line series," Rich writes, "it tells so much about an application in so little. While there are plenty of representative lines I could show about our application, I thought I’d show something else: a representative property."
"It’s a pattern we’ve termed the Bait & Switch Property."
The Tell-Tale Cable
by in Feature Articles on 2011-07-26As an experienced IT professional, Drew had seen his fair share of network outages over the years. He had protected his company’s network from storms, earthquakes, and even floods, but more often than not, the problem was from within. His fellow coworkers found ways to bring down their computers far more frequently on their own, through a combination of sending virus-laden e-mails, unplugging cords, and in some cases just gross incompetence.
One afternoon, Drew was installing some software from the network onto an employee's computer when the system locked up for 10 seconds.
Encrypted XML
by in CodeSOD on 2011-07-25The vendor of a certain, seven-figure software package that Thijs B's company relied on just released a new version that was no longer end-user configurable. Well, technically, it was... it just required the purchase of a $100,000 "configuration tool" instead of simply editing an XML file. While dropping $100K isn't too bad for most companies in the seven-figure software market, this particular company was frugal and thought it'd be worth investing some time before dropping a giant wad of cash. So, it was up to Thijs to see if the product was still configurable without the new tool.
Thijs opened up the familiar fieldset.xml file, but instead of finding a convoluted — but human-readable — mess of XML, he found this:
On-ramp to the Information Superhighway
by in Souvenir Potpourri on 2011-07-22Ever since the first Free Sticker Week ended back in February '07, I've been sending out WTF Stickers (and, now mini-buttons) to anyone that mailed me a SASE or a small souvenir. More recently, I've been sending out the coveted TDWTF Mugs for truly awesome souvenirs. Nothing specific; per the instructions page, "anything will do." Well, here goes anything, yet again! (previous: Assortment of Awesomeness).
When I received a fairly large package from Hans Van Slooten (Chicago, IL), I was super-excited. And then I opened it:
Three for Three, Recursion Threads, and Wrong Answer
by in Tales from the Interview on 2011-07-21Three for Three (from Randall C)
My boss, Harry, needed to hire some experienced software engineers, so he placed a job ad and did some kind of sort on the fifty or so replies that came in. Later, many of us assumed that he must have done a stair sort (throw them from the top of a stair and pick the ones that traveled farthest). He then said to me "I need to hire two engineers and I've selected three candidates. Would you like to interview them?" Not actually stated in this, but his attitude clearly indicated that he planned to hire two engineers from that pool of three.
I was willing to participate in the selection process so he set up a schedule for three interviews, Tim on Thursday, Charles on Friday, and Terry on Monday. This would be a lightweight responsibility for me and I would talk to the candidates over a free lunch. Well, okay. I was known to terrorize candidates by asking difficult questions and I could usually form an opinion based on a short discussion.
Not Non-uninvisible, addfunk(), and More
by in Coded Smorgasbord on 2011-07-20"I just inherited a PHP application and discovered this," writes David Green. "I don't know what's worse: the fact that it says add but is performing subtraction, or that I can't find the accompanying addnoise() function."
public function addfunk($one, $two) {
$val = $one - $two;
return $val;
}
The Shapes
by in CodeSOD on 2011-07-18"Despite working at my company for a year and a half," Carlos Barbosa writes, "I'm still amazed at what I find in production."
"Most of it is either impressively bad, or just so damn ugly that even its creator would avert his eyes. But sometimes, I find just plain weird. This was one of those times."
A More Unique Identifier
by in Feature Articles on 2011-07-14"Oh for crying out loud," Jeremy heard his cubicle-neighbor Andy shout, followed by a string of not-so-family-friendly expletives. "It's yet another duplicate GUID!"
Jeremy was intrigued. "Duplicate" is perhaps the least likely problem for a Globally Unique Identifier. With more than 340 billion trillion quadrillion (and that's no typo) possible values, the probability of having two identical GUIDs is basically non-existent. The probability of having multiple duplicate GUIDs is smaller than winning the lottery twice. On the same day. For every lottery held in the world.
Turning the Lights Out
by in Bring Your Own Code on 2011-07-13Despite the eighty-hour weeks, the relatively low pay, and the constant threat of being whipped if you don’t code fast enough, there’s something appealing about developing videogames professionally. After all, if videogames are superfun, then being immersed in them fourteen hours a day is basically heaven.
Of course, I never had a real desire to find out and ended up sticking with “normal” programming throughout my career. While I could always code whatever I wanted to do on the side, I never thought I’d ever get paid to write a videogame. That is, until I got paid to write this:
Ajax in the Underworld
by in Feature Articles on 2011-07-12Chuck had plenty of time to wonder about the smooth jazz that played on their conference call system. The beatless clarinet noodling was probably supposed to sooth you while waiting for others to join the call. In practice, it was frustration as performed by Michael Bolton.
It was a sound Chuck had become very familiar with over the past few days. He was consulting with an outside contractor so that they would know the internal coding standards. The meetings were scheduled at hours most convenient in England, not the US, which meant some early mornings for Chuck. But that didn't mean anyone from Ajax Solutions actually bothered to come to the meetings. The first time, Roger, the product lead claimed that he had been stuck in traffic on the M180. The second, it wasn't in his Outlook. He didn't bother with an excuse the third time.
The Legacy Handover
by in CodeSOD on 2011-07-11It was supposed to be a simple handover. One legacy application that was about to be retired. Paul smiled and took full responsibility.
It wasn't the complete absence of any documentation that broke him. Nor the extended hours trying to get it to build and run on another PC while the PHB bombarded him with messages from the airport on his way to a week’s holiday. The odd C++ inheritance wasn't a problem, nor the home brewed string class. The massive data allocation did cause a few raised eyebrows but thankfully it didn't leak badly enough to fix just yet. After all, it was going to be retired just as soon as Paul could get it running on anybody else's machine and it only crashed once an hour. The custom logging API, while not unusual, was no worse than anything Paul had met before.
Supported Image Formats, The Dreaded Zebra, and The Un-fix
by in Feature Articles on 2011-07-07The Dreaded Zebra (from Eric)
Before the turn of the century, I was a field desktop support analyst at a large hospital system, which meant that I’d get escalations from the help desk to go out and physically check up on computers and printers. Being a hospital and all, we were required to rotate “on-call” shifts should emergencies arise.
One night, I received a support page at 3AM. After wiping the sleep from my eyes, I called the number and asked what the problem was.
The Pesky "e"
by in CodeSOD on 2011-07-06"As a general rule of thumb," writes Newman, "we ignore all build warnings. After all, the code complies... so why bother worrying about warnings?"
"We also ignore errors and exceptions. After all, you can just write On Error Resume Next or use Try/Catch blocks to make them go away."
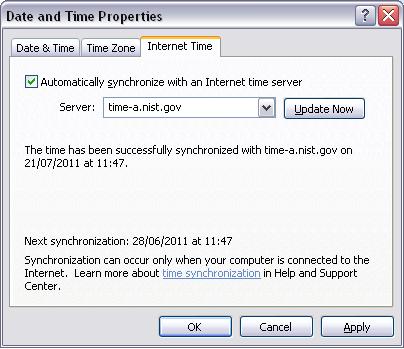
Trans-Atlantic Time Trap
by in Feature Articles on 2011-07-05Nobody believed the French. Not the entire country, or Frenchmen in general, but rather the folks who worked at the European Branch Office in Paris. The bug they described-their computer's internal date was randomly changing-reeked of user error and seemed far too implausible to be caused by the corporate reporting system.
But the French employees relentlessly called app support whenever their clock would mysteriously change. It was always a predictable dialog.

 Jun 11
Jun 11