Validating a Date with a Sledgehammer
by Mark Bowytz
in CodeSOD
on 2008-12-15
I think that it goes without saying that handling freeform user input, no matter the programming language, can be a tricky endeavor. Having to work with code like today's SOD makes me appreciate the pain felt by this bit of code Catherine Palmer inherited.
Now, I won't say that this function is necessarily terrible code, but when you consider that the field that code is intended to handle demands (in big red text) the entry of a date in a specific format (DD/MM/YYYY to be exact) and that it's meant to prevent a user from entering a date in the future, it'll leave you wondering why "TONY B" chose this exact plan of attack.
<script language="JavaScript">
<!--
function validate_futuredate(userdate)
//--- THIS DATE VALIDATION WAS DESIGNED BY ----//
//--- TONY B------- ON 02/05/2000 -----//
{
//---- get user date ---------------//
dday = userdate.value.substring(0,2)
mmnth = userdate.value.substring(3,5)
yyear = userdate.value.substring(6,10)
//--- get system date ---------------
curdate = new Date()
curyear = curdate.getFullYear()
curday = curdate.getDate()
curmonth = curdate.getMonth()
curmonth ++
//--- add one dayto curmonth as function produces zero for january ---//
strday=String(curday).length
strmonth=String(curmonth).length
//--- check that system day and month length greater 1 if not insert zero ---//
if (strday == 1)
{
curday = "0" + String(curday)
}
if (strmonth == 1)
{
curmonth = "0" + String(curmonth)
}
//--- create todays date to write back to input box on user input error ---//
ddate1 = curday + "/" + curmonth + "/" + String(curyear)
//--- get length and value of user input date ---//
posit = userdate.value
poslen = posit.length
//--- check date contains 10 characters ---//
if(poslen != 10)
{
alert("date contains wrong number of characters default value set")
userdate.value = ddate1
userdate.focus()
return (false)
}
//--- get first character of date make sure its less than 4 ---//
posit0 = userdate.value.charAt(0)
if (posit0 < "0" || posit0 > "3")
{
alert("date contains invalid DAY default value set")
userdate.value = ddate1
userdate.focus()
return (false)
}
posit1 = userdate.value.charAt(1)
if (posit1 < "0" || posit1 > "9")
{
alert("date contains invalid DAY default value set")
userdate.value = ddate1
userdate.focus()
return (false)
}
if (posit1 == "0" && posit0 == "0")
{
alert("date contains invalid DAY default value set")
userdate.value = ddate1
userdate.focus()
return (false)
}
if (posit0 == "3" && posit1 > "1")
{
alert("date contains invalid DAY default value set")
userdate.value = ddate1
userdate.focus()
return (false)
}
posit5 = userdate.value.charAt(5)
posit2 = userdate.value.charAt(2)
if (posit2 != "/" || posit5 != "/")
{
alert("date missing forward / mark default value set")
userdate.value = ddate1
userdate.focus()
return (false)
}
posit3 = userdate.value.charAt(3)
if (posit3 < "0" || posit3 > "1")
{
alert("date contains invalid MONTH default value set")
userdate.value = ddate1
userdate.focus()
return (false)
}
posit4 = userdate.value.charAt(4)
if (posit4 < "0" || posit4 > "9")
{
alert("date contains invalid MONTH default value set")
userdate.value = ddate1
userdate.focus()
return (false)
}
if (posit4 == "0" && posit3 == "0")
{
alert("date contains invalid MONTH default value set")
userdate.value = ddate1
userdate.focus()
return (false)
}
if (posit3 == "1" && posit4 > "2")
{
alert("date contains invalid MONTH default value set")
userdate.value = ddate1
userdate.focus()
return (false)
}
posit6 = userdate.value.charAt(6)
if (posit6 != "2")
{
alert("date contains invalid YEAR default value set")
userdate.value = ddate1
userdate.focus()
return (false)
}
posit7 = userdate.value.charAt(7)
if (posit7 != "0")
{
alert("date contains invalid YEAR default value set")
userdate.value = ddate1
userdate.focus()
return (false)
}
posit8 = userdate.value.charAt(8)
posit9 = userdate.value.charAt(9)
if (posit8 < "0" || posit8 > "9" || posit9 < "0" || posit9 > "9")
{
alert("date contains invalid YEAR at position9/10 default value set")
userdate.value = ddate1
userdate.focus()
return (false)
}
if (dday == "31" && (mmnth == "04" || mmnth == "06" || mmnth == "09" || mmnth == "11"))
{
alert("wrong number of days in specified MONTH default value set")
userdate.value = ddate1
userdate.focus()
return (false)
}
if (dday > "28" && mmnth == "02" )
{
alert("wrong number of days in specified MONTH default value set")
userdate.value = ddate1
userdate.focus()
return (false)
}
if (yyear > curyear)
{
alert("future dates are not allowed")
userdate.value =ddate1
userdate.focus()
return(false)
}
else if (yyear == curyear)
{
if(mmnth > curmonth)
{
alert("future dates are not allowed")
userdate.value =ddate1
userdate.focus()
return(false)
}
else if (mmnth == curmonth)
{
if (dday > curday)
{
alert("future dates are not allowed")
userdate.value =ddate1
userdate.focus()
return(false)
}
}
}
return(true)
}
//-->
</script>

 Nov 08
Nov 08









 When Nick Martin arrived at work at 8:30am, it seemed like he was in for a good day. Warm bagel and coffee in hand, he strolled into the IT office ready to fire up his email and maybe do a little recreational surfing before jumping into a day's worth of work. However, this was not meant to be as he was greeted by a support issue already in progress. And by "greeted", I mean "a dreary mess of a woman in a pinstripe suit was storming his way". It was Darlene, a manager from the university's financial department and conveniently, he was the only warm body in the office.
When Nick Martin arrived at work at 8:30am, it seemed like he was in for a good day. Warm bagel and coffee in hand, he strolled into the IT office ready to fire up his email and maybe do a little recreational surfing before jumping into a day's worth of work. However, this was not meant to be as he was greeted by a support issue already in progress. And by "greeted", I mean "a dreary mess of a woman in a pinstripe suit was storming his way". It was Darlene, a manager from the university's financial department and conveniently, he was the only warm body in the office.

 "Alright! 11:02 a.m...Another five bucks for me!"
"Alright! 11:02 a.m...Another five bucks for me!"
 Ray's life was out of control, but not in a bad way – it was just that everything was happening all at the same time. His wife was in her eighth month of pregnancy, so they were back and forth at Lamaze classes, babyproofing, and converting the spare bedroom into a nursery. Not to mention that Ray had received a better job offer and accepted, meaning that he had two weeks of transition at his old job and would have to hit the ground running as an admin at the new place.
Ray's life was out of control, but not in a bad way – it was just that everything was happening all at the same time. His wife was in her eighth month of pregnancy, so they were back and forth at Lamaze classes, babyproofing, and converting the spare bedroom into a nursery. Not to mention that Ray had received a better job offer and accepted, meaning that he had two weeks of transition at his old job and would have to hit the ground running as an admin at the new place.
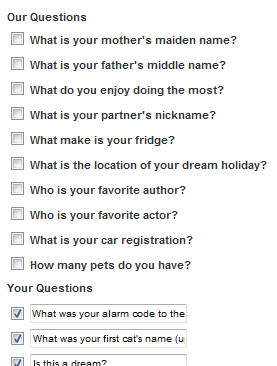 Not too long ago, Eric J. signed up for Thawte’s
Not too long ago, Eric J. signed up for Thawte’s  Sebastian sat near a window, enjoying a hot dog in the warmth of the sun. The day was going wonderfully so far – he was the first to get to the newspaper that was left in the break room daily (and usually gutted by noon), he'd found a quarter face up near his desk, and his hot dog was particularly good since someone had left relish in the fridge with a note inviting anyone to help themselves. At first, he hardly noticed the hurried, heavy footsteps coming in behind him – "My f–cking VPN connection is broken again! Can't you stop fiddling with the god damn network‽"
Sebastian sat near a window, enjoying a hot dog in the warmth of the sun. The day was going wonderfully so far – he was the first to get to the newspaper that was left in the break room daily (and usually gutted by noon), he'd found a quarter face up near his desk, and his hot dog was particularly good since someone had left relish in the fridge with a note inviting anyone to help themselves. At first, he hardly noticed the hurried, heavy footsteps coming in behind him – "My f–cking VPN connection is broken again! Can't you stop fiddling with the god damn network‽" Fresh out of school, Maxim was able to score himself a pretty sweet entry level position in a small private bank. Rather than being responsible for maintaining the company's static phone book on the corporate intranet or some other stereotypical entry level thing, he was placed in the understaffed Publications department to do some surprisingly heavy impacting IT work.
Fresh out of school, Maxim was able to score himself a pretty sweet entry level position in a small private bank. Rather than being responsible for maintaining the company's static phone book on the corporate intranet or some other stereotypical entry level thing, he was placed in the understaffed Publications department to do some surprisingly heavy impacting IT work.