The Key Lock Box
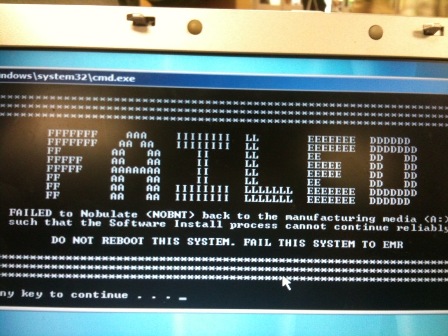
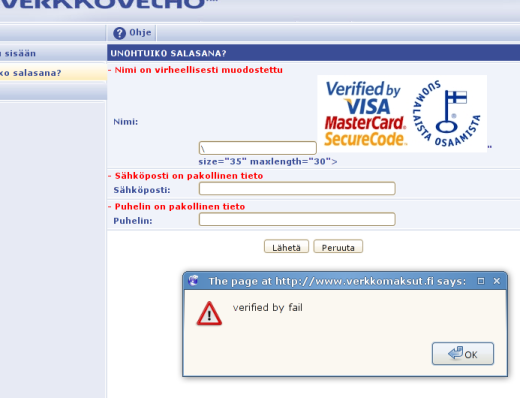
by in Bring Your Own Code on 2010-03-31 Nearly two years ago, I set out on the quest for a new house. Well, not new by any stretch of the word "new", but more foreclosed and dilapidated. It was 2008 and the market was flooded with homes, especially those of the not quite livable variety. As I explored house after house after house, I became intimately familiar with a device known as a key lock box. Generally used by realtors, key lock boxes are a convenient, low-tech way to provide combination code access to a lock that would otherwise require a physical key for access.
Nearly two years ago, I set out on the quest for a new house. Well, not new by any stretch of the word "new", but more foreclosed and dilapidated. It was 2008 and the market was flooded with homes, especially those of the not quite livable variety. As I explored house after house after house, I became intimately familiar with a device known as a key lock box. Generally used by realtors, key lock boxes are a convenient, low-tech way to provide combination code access to a lock that would otherwise require a physical key for access.
This was actually the first time I had ever seen a key lock box. Essentially, they're small steel boxes that contain a key and are often affixed near a keyhole (eg., the door handle). Some feature a set of dials that must be aligned with the right code, while others (such as the one pictured) use a pushbutton system to enter the combination.

 Feb 10
Feb 10



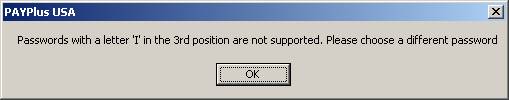
 When Hassan joined Meteor's IT department in 2006, he was pleasantly surprised to find everyone abuzz with excitement.
When Hassan joined Meteor's IT department in 2006, he was pleasantly surprised to find everyone abuzz with excitement.